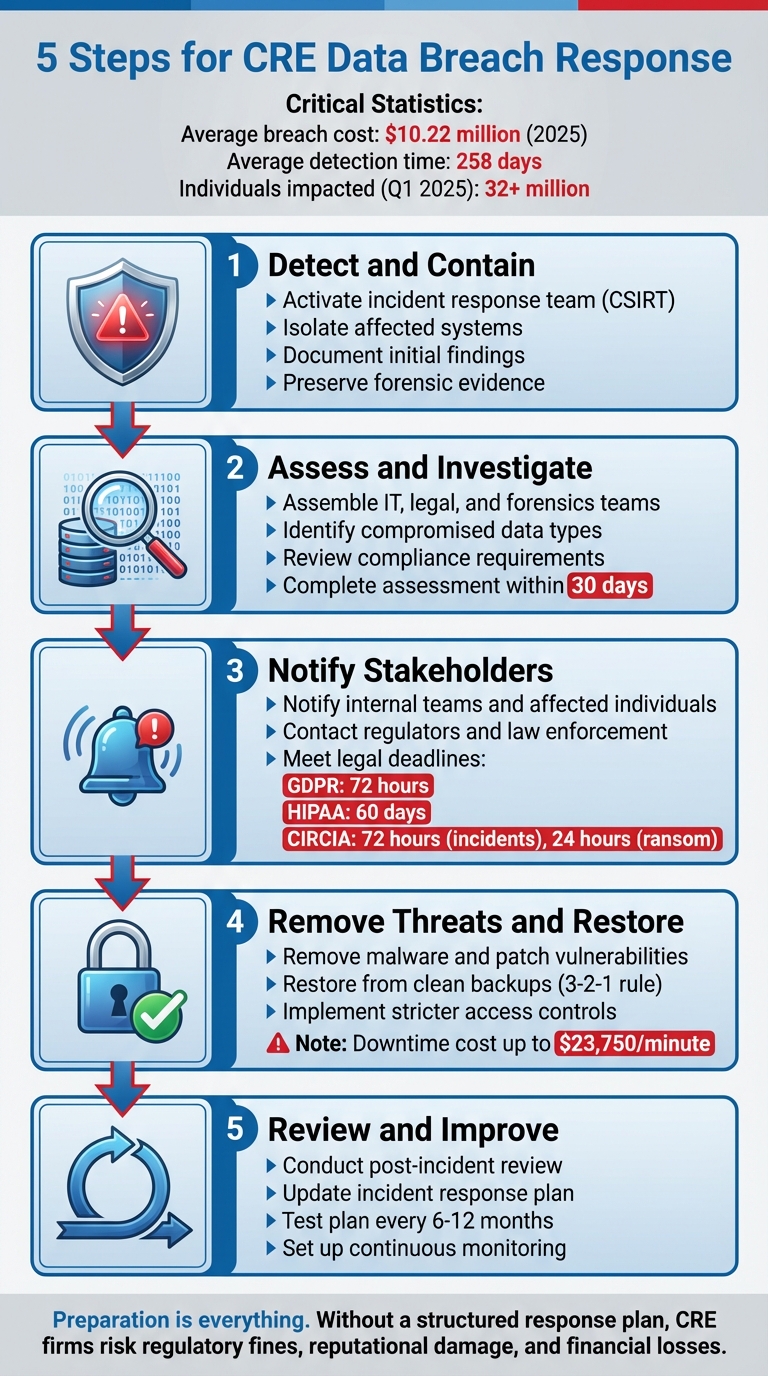
5 Steps for CRE Data Breach Response
- Why It Matters: CRE firms manage sensitive tenant, financial, and proprietary data, making them prime targets for cyberattacks. In 2025, the average U.S. data breach cost reached $10.22 million, with over 32 million individuals impacted in just three months.
- The Risks: Breaches expose Social Security numbers, financial records, and lease agreements, while also threatening intellectual property like appraisals and market analyses. Internal and external threats both pose significant challenges.
- Response Time is Critical: Companies take an average of 258 days to detect and contain breaches. Delays amplify financial and operational damage.
The 5 Key Steps for CRE Data Breach Response:
- Detect and Contain: Act swiftly to confirm and isolate breaches. Activate your incident response team and secure affected systems.
- Investigate: Assess the scope of the breach, identify compromised data, and review compliance obligations.
- Notify Stakeholders: Inform tenants, partners, and regulators within required deadlines. Clear communication rebuilds trust.
- Eliminate Threats: Remove vulnerabilities, patch systems, and restore operations securely.
- Review and Improve: Conduct a post-incident review to refine your response plan and strengthen defenses.
Quick Takeaway:
Preparation is everything. Without a structured response plan, CRE firms risk regulatory fines, reputational damage, and financial losses. Proactively train your team, establish clear protocols, and secure your data to minimize the fallout of future breaches.
5-Step CRE Data Breach Response Framework
Incident Response Plan: Security Breach Procedures
Step 1: Detect and Contain the Breach
The moment you suspect a breach, act swiftly to confirm it and stop it from spreading. Identify the systems that have been compromised - whether it’s a laptop, a database, or a server holding underwriting files. Figure out if the breach was caused internally or externally, whether it was intentional or accidental, and whether sensitive data like Social Security numbers or financial records has been exposed [2]. These initial steps lay the groundwork for a thorough investigation and any required notifications.
Activate Your Incident Response Team
Get your Computer Security Incident Response Team (CSIRT) into action immediately. This team, which should already be in place, includes IT experts, legal advisors, and management coordinators who can bridge the gap between technical issues and business risks [6]. If your IT systems are compromised, switch to secure communication methods like telephones - attackers could be monitoring your internal networks [2].
"A well-designed incident response plan can be the crucial differentiator that lets an organization quickly contain the damage from an incident and rapidly recover normal business operations." - TechTarget [6]
Isolate Affected Systems
Quickly disconnect any compromised systems to prevent further access. Update all passwords, remove administrative privileges, and change access codes across impacted systems [2]. If malware is involved, disable it immediately. For physical breaches, like a stolen hard drive containing tenant information, secure the area and change physical locks or access codes [2]. While doing this, be sure to preserve system images and any forensic evidence - don’t shut down systems in ways that could erase volatile data [4].
Document Initial Findings
From the moment the breach is detected, start keeping a detailed log. Record who discovered it, how it was detected, and the exact time it occurred [2]. Document what kind of data was compromised, such as names, financial records, or lease agreements, and note whether the data was encrypted and how many records were affected. Keep a record of every action taken by your team, including who performed it and when [2]. This documentation is not only critical for legal compliance under regulations like HIPAA but also for meeting notification deadlines, which can be as short as 30 days under certain rules [2][4].
"Each data breach response needs to be tailored to the circumstances of the incident." - OAIC [4]
Step 2: Assess and Investigate the Breach
Once the immediate threat is contained, the next step is to dig into the details of what happened. This investigation helps uncover the full scope of the breach - what data was compromised and how the attacker gained access. The insights you gather will guide critical decisions, from notifying affected parties to strengthening your defenses. A thorough assessment lays the groundwork for clear communication with stakeholders and a smoother recovery process.
Bring in IT, Legal, and Forensics Teams
Quickly assemble your IT, legal, and forensic experts to piece together how the breach occurred. Conduct the investigation under attorney-client privilege to keep sensitive findings protected[2].
"Data breach response is usually not purely linear because these stages and the activities associated with them frequently overlap."
Identify Compromised Data
Determine exactly what data was accessed or stolen. In the commercial real estate (CRE) sector, this could include tenant records, rent rolls, financial models, lease details, or property analytics[2]. For complex documents, such as intricate leases, consider using AI-driven tools to quickly identify hidden risks or unusual clauses that may have been exposed[7]. Check your system logs to confirm whether the data was merely viewed or also exfiltrated. Additionally, verify if the affected files were encrypted and whether encryption keys were compromised[2].
"Breaches that may initially seem immaterial may be significant when their full implications are assessed."
- OAIC[4]
Review Compliance and Notification Requirements
Determine which regulations apply based on the type of data and the jurisdictions involved. For example, you might need to comply with state-specific laws like the California Consumer Privacy Act (CCPA), sector-specific rules such as SEC requirements for public companies, or contractual obligations tied to tenants or business partners[2]. If you're governed by the National Data Breach scheme, aim to complete your assessment within 30 days[4]. Work with legal counsel to identify when notifications are legally required, as these depend on the sensitivity of the data and the state’s specific laws[2]. Also, review your cyber insurance policy to understand what’s covered and any obligations involving third-party vendors[2].
Step 3: Notify Stakeholders
Once your investigation is complete, the next step is to notify all relevant parties promptly and transparently. This step is crucial not just to limit further harm but also to comply with legal obligations. Effective communication helps maintain trust with tenants, investors, and partners while adhering to strict deadlines.
Determine Who Needs to Be Notified
Start by identifying all necessary stakeholders. These typically include internal teams such as leadership, legal, and IT, as well as affected individuals like tenants and employees. Don’t forget external parties such as investors, regulators, law enforcement, and contractual partners.
It's also essential to loop in financial and legal stakeholders, including business partners, insurance carriers, and investors, as they need to evaluate the financial impact and assess coverage. Notify regulatory bodies and law enforcement, such as state Attorneys General or industry-specific regulators like the SEC for public companies. If the breach involves data maintained on behalf of third parties, contact those data owners immediately to decide who will handle notifying individuals. Finally, review leases and service agreements to ensure you meet any contractual notification requirements for tenants or partners.
Once you've identified the relevant groups, prioritize delivering clear, consistent, and timely communication.
Write Clear and Honest Communications
Your communication should be straightforward, sensitive, and tailored to the audience. Consider setting up resources like a toll-free hotline, call scripts, and an FAQ page to address concerns effectively. Tailor your messages for tenants, investors, and even the media to ensure they are appropriate for each group.
"Notification has the practical benefit of providing individuals with the opportunity to take steps to protect their personal information following a data breach, such as by changing account passwords or being alert to possible scams."
- OAIC[4]
Before making public statements, consult with law enforcement to avoid jeopardizing investigations. Prepare media holding statements ahead of time so you can respond quickly if news of the breach leaks before formal notifications are sent. It's important to remember that identity theft or fraud related to a data breach can sometimes surface months, or even over a year, after the incident [8].
Meet Legal Notification Deadlines
Timing is everything when it comes to legal notifications. For example, the GDPR mandates notifying authorities within 72 hours of discovering the breach [10]. HIPAA, on the other hand, requires notification within 60 days [9]. If you're subject to the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA), you must report major cyber incidents to CISA within 72 hours and any ransom payments within 24 hours [11].
| Regulation | Authority Notification | Individual Notification |
|---|---|---|
| GDPR | 72 hours after becoming aware [10] | Immediately if high risk [10] |
| HIPAA | 60 days from discovery [9] | 60 days from discovery [9] |
| CIRCIA | 72 hours for incidents; 24 hours for ransom [11] | N/A (Federal reporting focus) |
| State Laws | Typically 30 to 60 days [11] | Varies by state [5] |
Keep in mind that these deadlines start ticking the moment the breach is detected [9]. Missing them can lead to severe penalties. For instance, under GDPR, failing to notify within 72 hours can result in fines as high as €10 million or 2% of your global annual revenue [10].
sbb-itb-99d029f
Step 4: Remove Threats and Restore Operations
After informing stakeholders, the next step is eliminating the threat and getting your systems back up and running. This phase demands precision - rushing to recover without addressing the root causes can leave your organization open to reinfection. Attackers often maintain access for months if recovery efforts are incomplete or hurried [12].
Remove Threats and Patch Vulnerabilities
Start by isolating affected machines, preserving forensic evidence, and revoking compromised privileges. If necessary, secure physical access to systems to prevent further tampering [2][12]. Deactivate malware or any suspicious software, reset all credentials, and revoke active tokens. Additionally, rotate encryption keys for any accounts tied to the compromised systems [12].
"If it is not practical to shut down the system, or if it would result in loss of evidence, then revoke or change computer access privileges or address weaknesses in physical or electronic security."
- OAIC[4]
Conduct a root cause analysis to pinpoint how attackers gained entry. This step is essential - without understanding the initial breach, you risk leaving vulnerabilities exposed [4]. Once identified, apply security patches to affected systems and update outdated software or hardware to close the gaps [2].
After neutralizing the threats and addressing vulnerabilities, the focus shifts to restoring your systems safely.
Recover Data and Systems
When bringing systems back online, use clean, hardened system images instead of simply rebooting compromised ones [12]. This ensures that no malicious files are inadvertently reintroduced. Follow the 3-2-1 backup rule: maintain three copies of your data, store them on two different media types, and keep one copy off-site [12]. Before reconnecting systems to your production network, verify the integrity of restored data using hash comparisons or similar methods [12].
The cost of unplanned downtime can reach as high as $23,750 per minute, so take the time to verify all restored systems thoroughly before they go live [12]. Continue monitoring these systems for any signs of reinfection to ensure they are fully operational and secure [12].
Once operations are restored, it's time to strengthen your defenses to prevent future breaches.
Strengthen CRE-Specific Security Measures
Commercial real estate firms handle highly sensitive data - digital leases, rent rolls, financial statements, and appraisals that include detailed financial information about properties, tenants, and investors [1]. To protect this data, implement stricter access controls based on "need-to-know" principles [2][4].
Consider using platforms like CoreCast to centralize access controls and securely manage transaction data. With 72% of real estate owners and investors now leveraging AI-powered tools [13], solutions that consolidate underwriting, pipeline tracking, portfolio analysis, and stakeholder reporting into one secure system can reduce the risk of data fragmentation. CoreCast’s integrated approach limits access points for attackers and enforces role-based permissions, ensuring team members only access the data they need.
Audit your third-party partners and vendors, especially those potentially involved in the breach [4]. Evaluate their security practices and update service agreements to include stricter data protection standards. Implement continuous monitoring and conduct regular audits to ensure your new measures remain effective [4].
"A data breach should be considered alongside any similar breaches that have occurred in the past, which could indicate a systemic issue with policies or procedures."
- OAIC[4]
Step 5: Review and Update Your Response Plan
Getting your systems back online and neutralizing threats is just the beginning. Each data breach is an opportunity to identify weaknesses, strengthen defenses, and refine your response strategies. Without a structured review process, you might miss critical lessons or repeat past mistakes, leaving your organization vulnerable to future incidents.
Conduct a Post-Incident Review
Hold a thorough post-incident review with your response team, including IT staff, legal advisors, forensic experts, and leadership. This meeting should focus on what worked, what didn’t, and where your security measures fell short [6]. Document key details like the root cause of the breach, the time it took to detect the issue, and which systems were affected [14].
"Incident response plans should require a formal lessons-learned session at the end of every major security incident... This enables an organization to reduce the likelihood of future incidents and improve its ability to handle incidents that do occur."
- Paul Kirvan, Independent Consultant and IT Auditor [6]
Take the time to conduct a detailed gap analysis of your security controls. This will help you identify the technical or procedural weaknesses that allowed the breach to happen or delayed your response [6]. For commercial real estate firms, this might mean examining how sensitive documents like lease agreements or rent rolls are accessed and shared. These insights are critical for updating your response plan effectively.
Update Your Incident Response Plan
Think of your incident response plan as a dynamic document that evolves with every new challenge. Use the findings from your review to address gaps in processes, communication channels, or decision-making authority [6][14]. Update your playbooks with clear, actionable steps tailored to specific threats like ransomware attacks or insider breaches [6].
Testing your revised plan is equally important. Conduct these tests at least once a year - or even every six months - to keep up with emerging threats [6][14]. Combine tabletop exercises, where teams discuss procedures, with operational drills that simulate real-world scenarios. This approach builds the "muscle memory" your team needs to act quickly and effectively when it matters most [6][14].
"Post-mortem processes are essential to learn from every incident and continuously improve the process, making the incident response plan a living document."
By continuously refining your plan, you’ll be better prepared for whatever comes next.
Set Up Continuous Monitoring and Audits
Preventing future breaches isn’t a one-and-done effort - it requires constant vigilance. Implement advanced monitoring tools that use analytics and automation to sift through data, freeing up your security team to focus on more critical investigations [14]. AI-driven tools can also help with ongoing analysis of lease documents and rent rolls, which is especially useful for commercial real estate professionals [7].
Strengthen your audit measures to ensure compliance with regulations and to maintain a reliable audit trail for potential investigations [2][6]. Align your monitoring and auditing processes with established frameworks like NIST SP 1800-29, which focuses on detecting and recovering from data confidentiality breaches [3]. For real estate professionals, this level of vigilance not only safeguards sensitive financial and tenant information but also reinforces trust among investors, partners, and tenants.
If your firm uses platforms like CoreCast, integrating real-time monitoring tools can further enhance your security efforts. By treating security as a strategic priority rather than just a compliance requirement, you’ll reduce risks and build a stronger foundation for future growth [7].
Conclusion: Prepare Now for CRE Data Security
Data breaches can damage investor relationships, erode tenant trust, and tarnish a firm's reputation. This guide provides a step-by-step framework to help you respond effectively when incidents arise. The key, however, lies in treating these steps as part of a proactive strategy rather than a last-minute reaction.
A well-coordinated response is essential for handling breaches swiftly. Since data breach responses are rarely straightforward, having a cross-functional team ready - comprising IT, legal, forensic, and communications experts - ensures your organization can act immediately when a breach is detected [2]. Pre-prepared communication tools and secure channels further enable quick, confidential notifications without risking additional data exposure [2].
Organizations that excel in security focus on continuous improvement through regular audits and updates to their response plans [4]. These practices not only help identify vulnerabilities but also ensure lessons from past incidents are applied. As the Office of the Australian Information Commissioner points out:
"Notification can also help build trust in an entity, by demonstrating that privacy protection is taken seriously" [4].
Platforms like CoreCast offer centralized data management and streamlined breach notification processes, boosting your overall security efforts. By consolidating incident logs and enabling secure communications, CoreCast supports both immediate responses and proactive risk mitigation. Strengthening your security measures today lays the foundation for resilient operations in the future.
The time to act is now. Develop a robust response plan, train your team, and leverage secure platforms to safeguard critical data and protect your organization from potential threats.
FAQs
What steps should commercial real estate firms take immediately after a suspected data breach?
If you suspect a data breach, the priority is to act fast to limit the damage and protect sensitive information. Begin by isolating the impacted systems to block any further unauthorized access. If necessary, secure physical locations tied to the breach. Assemble a response team that includes IT experts, legal advisors, and cybersecurity professionals to manage the situation effectively.
Make sure to preserve all evidence related to the breach. This will be crucial for identifying its cause and meeting any legal or regulatory obligations. At the same time, evaluate the extent of the breach to determine which data or systems were affected. Quick action on these fronts can help contain the problem and pave the way for recovery while ensuring clear communication with stakeholders.
How can commercial real estate firms comply with data breach notification laws?
To meet data breach notification laws, CRE firms need a response plan tailored to regulations. Start by identifying all relevant laws, including federal mandates like the FTC’s Safeguards Rule, state-specific breach notification requirements, and industry-focused regulations such as HIPAA. Create a comprehensive inventory of the personal data your firm manages and align it with these rules. This helps determine when a breach requires notification and identifies the authorities that must be informed.
Craft a detailed breach response plan that covers critical steps like containment, assessing the breach, issuing timely notifications, and conducting post-incident evaluations. Include specific timelines, such as notifying affected individuals within 30 days (as required by most states) or within 60 days for HIPAA compliance. Maintain a thorough incident log to track every action taken, ensuring you meet record-keeping standards and are prepared for audits.
Tools like CoreCast can simplify the process by automating notification tracking, generating reports tailored to specific regulations, and securely preserving evidence. This not only helps avoid missed deadlines and potential penalties but also demonstrates to regulators that your firm takes a structured and proactive approach to safeguarding data.
What are the best ways to improve security and prevent data breaches in the commercial real estate (CRE) industry?
Improving security in the commercial real estate (CRE) sector begins with getting a clear handle on your data. Start by identifying all your data sources - things like client records, lease agreements, and financial models - and sort them based on their sensitivity. From there, put a solid data-security plan in place. This should include tools like encryption, multi-factor authentication, and role-based access controls. Don’t forget to keep software and systems updated and use monitoring tools to catch any unusual activity before it becomes a bigger problem.
But technology alone isn’t enough. Human and procedural factors play a huge role in security. Train your team to spot phishing scams and stick to secure coding practices. Run regular breach response drills with a team that includes IT, legal, and senior management. Also, hold your vendors to high security standards and check in on their compliance regularly. Platforms like CoreCast, which offer centralized data management, can make this process easier by providing detailed permissions and audit trails to help you enforce policies and quickly flag risks.
By pairing strong technical measures with smart policies and ongoing training, CRE firms can significantly reduce their risk of data breaches.

